Step 5: Shifting Left and Prioritization
When new vulnerabilities seem to outpace our resources to mitigate them, we need to optimize our security efforts. In this step we address this challenge by advocating for early integration of security within the development lifecycle and smart vulnerability prioritization. Utilizing metrics like the Exploit Prediction Scoring System (EPSS), Common Vulnerability Scoring System (CVSS) Score, and well-defined policies enables organizations to ensure that critical vulnerabilities are addressed first.
Integrating Security Early in the Development Lifecycle
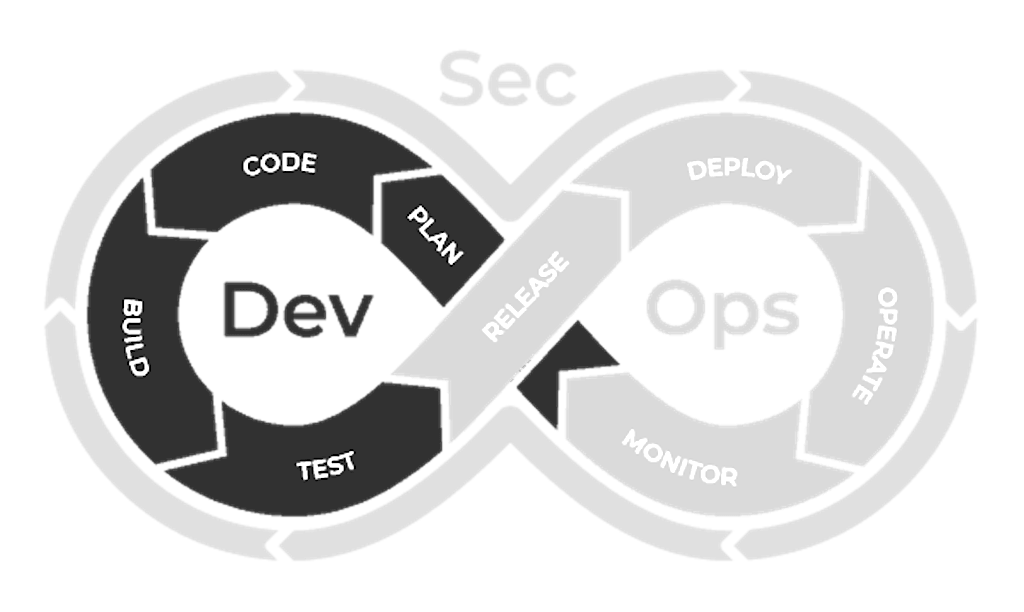
The Concept of Shifting Left
The DevSecOps philosophy embodies the principle of 'shifting left,' which emphasizes embedding security practices from the get-go of the software development process. This proactive stance ensures that security considerations are not afterthoughts but are integral from the design phase through to coding and testing.
Prioritizing Actions Based on Risk Assessment
With an ever-expanding array of vulnerabilities and threats, it's crucial to prioritize remediation efforts based on a comprehensive risk assessment. This ensures that resources are allocated efficiently, focusing on mitigating the most significant risks first.
Conducting a Risk Assessment
A risk assessment involves evaluating the potential impact and likelihood of vulnerabilities being exploited. This assessment should consider the criticality of the affected system, the sensitivity of the data involved, and the potential consequences of a breach.
Implementing a Prioritization Framework
Severity-Based Prioritization: Use established severity scoring systems, such as the Common Vulnerability Scoring System (CVSS), to rank vulnerabilities based on their potential impact.
Contextual Prioritization: Take into account the specific context of your organization, including the operational importance of the affected asset and the current threat landscape, to refine prioritization further.
Remediation Timelines: Establish clear timelines for remediation based on the priority level of each vulnerability, ensuring that high-priority issues are addressed promptly.
External threat signals: Other external analysis can be taken into consideration for prioritization. Metrics such as Exploit Prediction Scoring System (EPSS), which predicts the likelihood that a vulnerability will be exploited in the wild. OSSF Scorecard can be used to further evaluate risks that dependencies introduce,
Using SBOM Observer to shift left
The SBOM Observer framework significantly enhances the process of prioritization within an organization's cybersecurity strategy by leveraging critical metrics such as the Common Vulnerability Scoring System (CVSS) Score, the Exploit Prediction Scoring System (EPSS) score, and Vulnerability Exploitability eXchange (VEX) statuses.
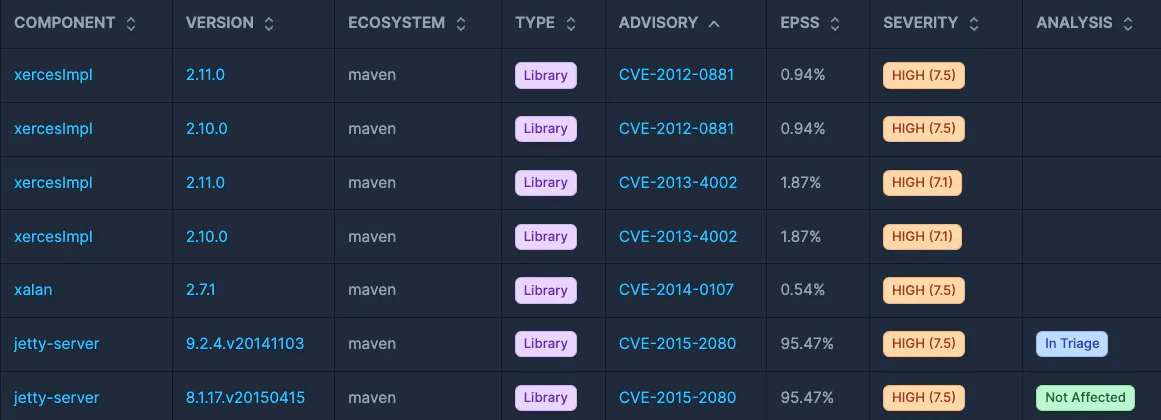
By integrating these metrics, SBOM Observer provides a nuanced and dynamic approach to assessing and prioritizing vulnerabilities. The CVSS Score offers a standardized severity rating of vulnerabilities, allowing organizations to quickly identify the most critical issues that need immediate attention.
The EPSS score, on the other hand, provides a probabilistic assessment of the likelihood that a vulnerability will be exploited, adding an important layer of risk analysis to the prioritization process.
Additionally, VEX statuses give insights into the applicability of vulnerabilities in the context of the specific environment, highlighting which vulnerabilities are actionable and which are not relevant due to mitigations or configurations.
Next Step
In the next step we explore how establishing clear security policies are a crucial cybersecurity risk management strategy.