Step 6: Defining Policies
In the quest to fortify an organization's cybersecurity posture, the establishment of coherent security policies and acceptable risk levels is paramount. This crucial step lays down the foundational guidelines that will steer the management of security risks and dictate the measures for their mitigation.
Crafting Effective Supply Chain Security Policies
Security policies serve as the cornerstone of a robust cybersecurity framework, delineating the strategies, protocols, and controls to safeguard against potential threats.
Principles of Effective Security Policy Development
Clarity and Accessibility: Ensuring policies are understandable and accessible to all relevant parties guarantees a unified approach to security.
Business Objective Alignment: Security measures must complement, not conflict with, the overarching goals of the organization.
Adaptability: The dynamic nature of cyber threats necessitates policies that can evolve in response to new security challenges and technological advancements.
Setting and Managing Risk Tolerance Thresholds
Identifying the organization's risk tolerance is critical, involving the delineation of acceptable risk levels in pursuit of business objectives.
Establishing Risk Tolerance Thresholds
These thresholds are defined by understanding the organization's risk appetite, the potential impact of security incidents, and the capacity for incident response and recovery. This facilitates focused mitigation efforts, channeling resources towards mitigating risks that surpass the organization's tolerance.
Start small
A well communicated concise policy is more valuable than a complicated that is understood by few.
"At Acme Inc. we address all known vulnerabilities of a CVSS Score of HIGH or greater within 7 days. If a vulnerability of public accessible components has an EPSS Score greater than 20% it must be mitigated within 24h. The Mean Time to Remediate (MTTR) for all detected vulnerabilities should be at most 14 days."
Leveraging SBOM Observer for Enhanced Policy Implementation
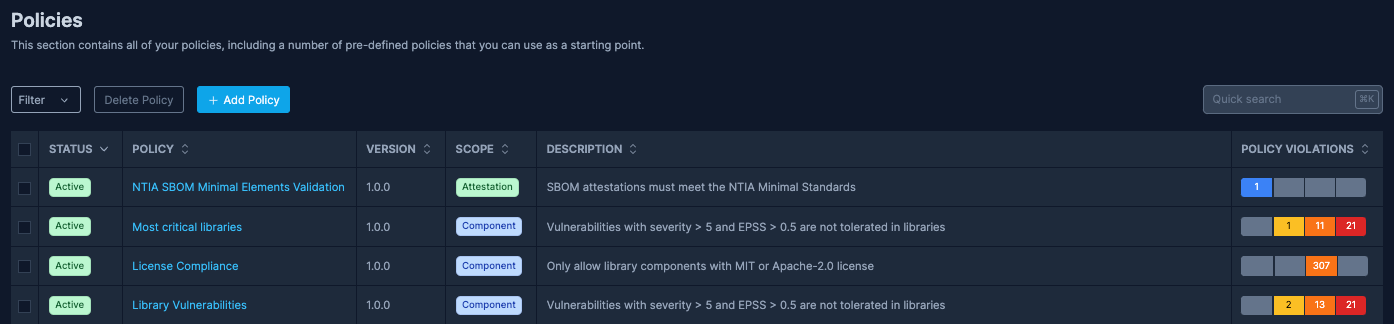
SBOM Observer supports policy as code which allows for security policies to be programmatically defined, presenting several key benefits:
Consistency and Precision: Policy as Code eliminates uncertainties and guarantees the consistent enforcement of security throughout the organization.
Seamless Automation: The automation of policy enforcement integrates security seamlessly into development and operational workflows, enhancing protection without disrupting productivity.
Dynamic Scalability: Policy adaptability is significantly improved, with the ability to swiftly modify or extend policies in reaction to emerging threats or operational changes.
Streamline Policy Enforcement: Integrating these policies within the CI/CD pipeline ensures that software deployments align with the organization's risk tolerance, automatically preventing the deployment of components that introduce unacceptable risks.
Read more about Policy as Code in SBOM Observer
SBOM Observer Rego policy example
The below example defines a strict policy that creates policy violations when breached.
The logic defines that, for a library, vulnerabilities with a CVSS score > 5 and an EPSS Score above 50% without any VEX explanation will raise an violation.
package observer
import future.keywords.in
violation[v] {
input.component.type == "library"
some vulnerabilitiy in input.vulnerabilities
vulnerabilitiy.severity > 5
vulnerabilitiy.epss > 0.5
# vex
not vulnerabilitiy.vex.state == "not_affected"
not vulnerabilitiy.vex.state == "false_positive"
not vulnerabilitiy.vex.state == "resolved"
not vulnerabilitiy.vex.state == "resolved_with_pedigree"
v := {
"severity": vulnerabilitiy.severity,
"message": sprintf(
"%s with severity>5 (%v) and EPSS>0.5 (%0.2f) is not tolerated",
[
vulnerabilitiy.vendorId,
vulnerabilitiy.severity,
vulnerabilitiy.epss,
],
),
}
}
Next Step
In the next step - Continuous Monitoring and Improvement we explore how establishing measurable KPIs, and leveraging tools like the SBOM Observer, organizations can ensure that their security measures are not only effective today but also adaptable to the challenges of tomorrow.