Step 7: Continuous Monitoring and Improvement
In the realm of cybersecurity, vigilance is not a one-time effort but a continuous process. The seventh step in enhancing an organization's cybersecurity posture involves the establishment of robust mechanisms for ongoing monitoring and the iterative improvement of security measures. This chapter discusses strategies for implementing continuous vulnerability management in the software supply chain.
Implementing Ongoing Vulnerability Management Strategies
The Foundation of Continuous Monitoring
Continuous monitoring is the systematic process of tracking and analyzing the security of an organization's information systems in real-time. This approach enables the early detection of vulnerabilities and threats, allowing for swift mitigation actions.
Automated Scanning and Analysis: Utilize automated tools to regularly scan systems and applications for vulnerabilities. This includes the integration of Software Composition Analysis (SCA) tools such as SBOM Observer to continuously monitor for new vulnerabilities in open-source components and libraries.
Integration with Development and Deployment Processes: Embed security checks into the CI/CD pipeline to ensure that every update or new release is scanned for vulnerabilities before deployment.
Threat Intelligence Feeds: Incorporate threat intelligence feeds to stay informed about new vulnerabilities and emerging threats. This information can be used to adjust monitoring parameters and prioritize responses based on the latest threat landscape.
Prioritizing Remediation Efforts
Not all vulnerabilities pose an equal threat; thus, prioritization is key. Utilize risk-based prioritization, factoring in the severity of the vulnerability, the criticality of the affected system, and the potential impact of an exploit. This approach ensures that resources are allocated efficiently, focusing on the most significant threats first.
Measuring and Enhancing Security Posture Over Time
Establishing Key Performance Indicators (KPIs)
To effectively measure the security posture and track improvements over time, establish clear KPIs. These may include:
Mean Time to Detect (MTTD): The average time it takes to detect a security issue or vulnerability.
Mean Time to Remediate (MTTR): The average time required to remediate a detected vulnerability.
Vulnerability Closure Rate: The rate at which identified vulnerabilities are remediated.
Leveraging SBOM Observer for Continuous Improvement
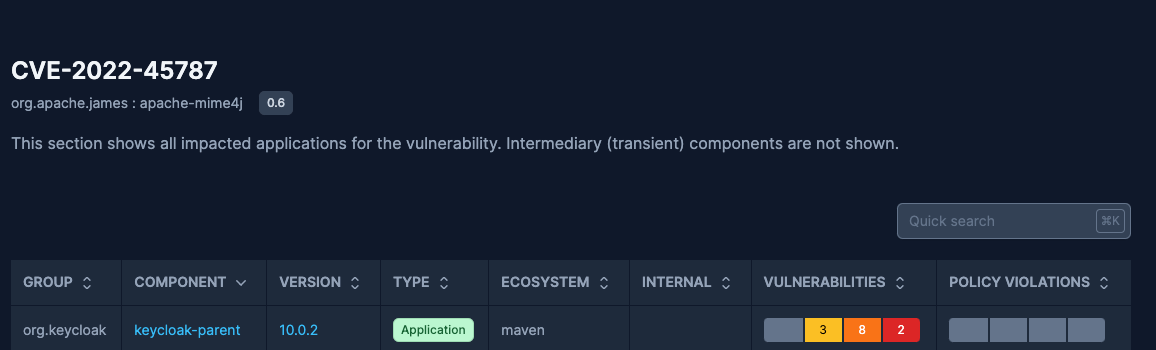
SBOM Observer facilitates the continuous improvement of an organization's security posture through:
Real-Time SBOM Updates: Ensure that the SBOMs are continuously updated to reflect the current state of software components, allowing for real-time vulnerability management. Read more about how to set up CI/CD integration.
Policy as Code: Utilize the Policy as Code capabilities to dynamically adjust security policies and controls based on the evolving threat landscape and organizational changes. Read more about Policy as Code
Next Step
In the next step - Sharing SBOMs we explore how sharing SBOMs enhances transparency and builds trust with customers.