Using SBOM Observer
SBOM Observer offers a robust SBOM workflow solution designed to optimize your software supply chain management. Benefit from the unmatched synergy of our Policy Engine and Operational Model to ensure improved security and compliance of your software.
This quickstart guide provides a concise walkthrough on initiating and navigating your SBOMs, either by manually uploading them or by seamlessly integrating them into your CI/CD pipeline.
Working with SBOM attestations
Uploading the first SBOM file
- Navigate and click on Attestations in the menu.
- Select the Upload Attestation button to upload your SBOM.
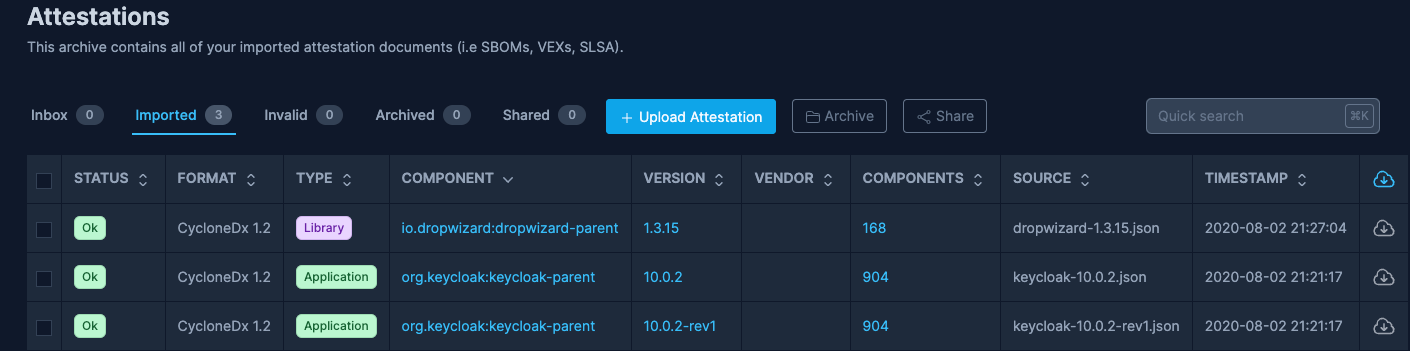
Supported SBOM formats
SBOM Observer supports both CycloneDX and SPDX.
For more details, navigate to Coverage and Compatibility.
If you're in search of CycloneDX SBOM sample files, you'll find a few in the official CycloneDX Git Repository. GitHub also provides functionality to export SBOMs in SPDX format for repositories, following these steps.
Vulnerabilities
Once you've uploaded an attestation, the SBOM Observer scans and identifies any potential vulnerabilities. To review them, simply click on the attestation you just uploaded. Then lastly click on the Vulnerabilities tab and toggle Include Dependencies if you want see vulnerabilities for the whole dependency tree.
From here you can read more details about the vulnerabilities. 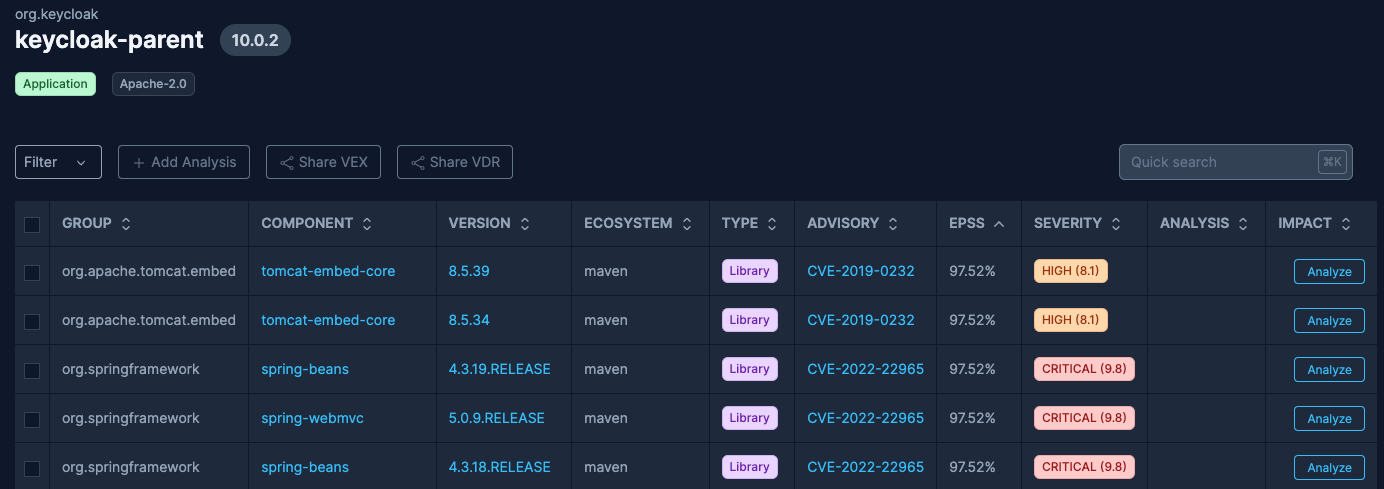
Impact analysis
To ascertain which of your components might be affected by a vulnerability:
- Search for a specific vulnerability och click on a specific component.
- Click on the Impact Analysis button corresponding to a particular vulnerability.
- A list will display the potentially impacted components.
- By selecting the Graph option, you can delve deeper into the details. If you've set up Environments, this data will also be evident in the Graph visualization. Be able to answer is a vulnerability impacts your production environment is quite nice.
Navigate to Impact Analysis for more details on how to understand vulnerability impact. 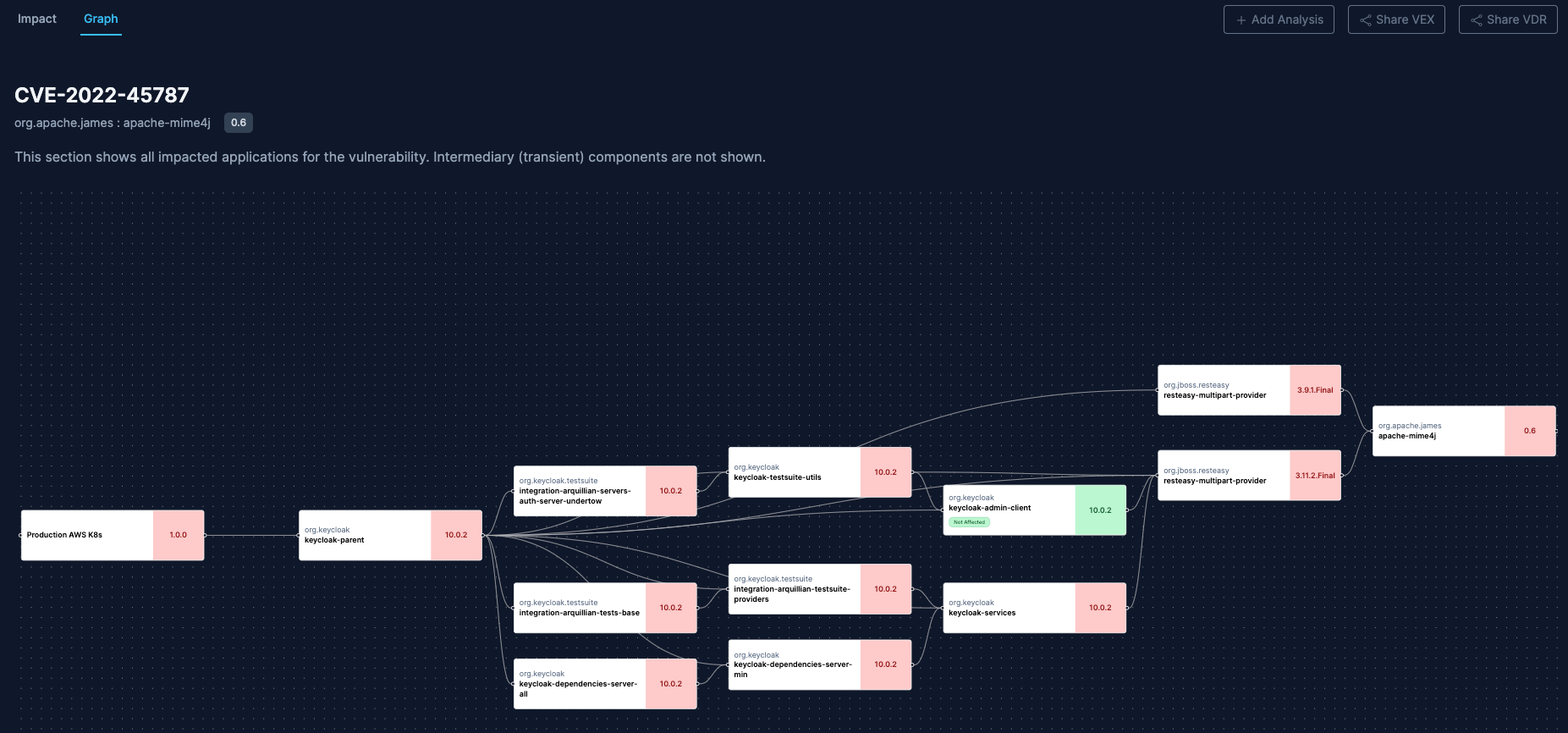
Using Environments
Using Environments is a quick way to connect your applications to a specific environment such as Production. This way you'll be able to respond to if a vulnerability impacts your specific environment, how many vulnerabilities you have in your environment etc.
You're able to enrich with information that is not present in SBOMs and use policies to make sure your applications in your different environments comply with your internal policies or regulations. 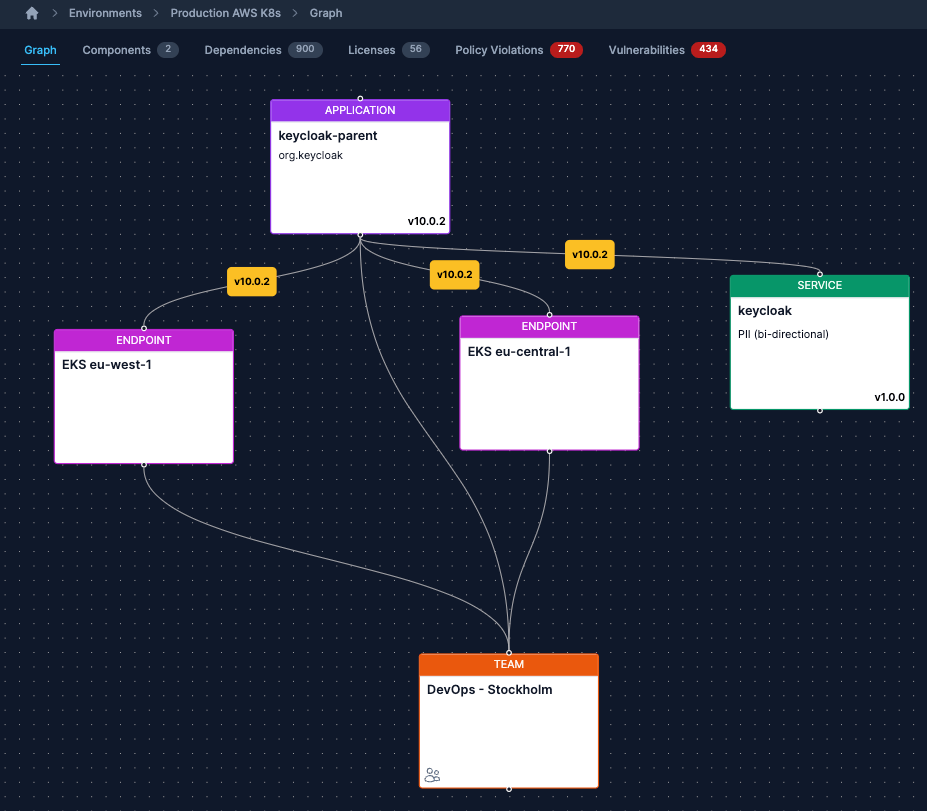
Using Projects
Projects in SBOM Observer are collections of components (applications, libraries, containers). Basically projects are shortcuts to specific views used by specific teams, software projects etc. to filter out relevant components.
Creating a Policy
Think of policies as the guidelines that keep your software in check. In SBOM Observer, policies allow you to establish specific rules and criteria that your software components must follow. This can encompass everything from security to licensing requirements. Implementing these policies ensures that all your software components consistently meet the standards you've set forth.
Navigate to Using Policies for more details on how to use the visual policy builder or write policies as code.
Automate your SBOM Workflow
Integrating SBOM Observer into your CI/CD pipeline ensures that software bills of materials are checked and managed automatically, streamlining the process and ensuring continuous compliance. And you make sure to archive all changes made in your environments.
Navigate to CI/CD Integration to what you need to do to integrate SBOM Observer with your build pipeline.