Implementing Supplier Transparency in SBOM Observer
Cybersecurity regulations globally underscore the importance of supplier transparency. The Digital Operational Resilience Act (DORA) is an example among many frameworks emphasizing this need. This guide provides a structured approach to improve cybersecurity by efficiently tracking and managing supplier components in SBOM Observer.
Step-by-Step Guide to Enhancing Supplier Transparency
Understanding and managing the risks associated with third-party suppliers is crucial in cybersecurity. Regulations such as DORA, NIS2, and Executive Order 14028 (EO14028) mandate this practice for effective risk management, compliance, and operational resilience.
Assuming you have an internal policy aligning with cybersecurity mandates like DORA and have engaged the appropriate stakeholders, this guide focuses on practical steps to start tracking supplier components in SBOM Observer.
1. Setting Up a Supplier Information Management System
- Identify Supplier Components: Determine which components in your ICT infrastructure are supplied externally.
- Gather Supplier SBOMs: Collect Software Bill of Materials (SBOMs) in formats like CycloneDX or SPDX for these components. Automation in gathering these SBOMs is ideal, as their widespread industry adoption makes this feasible.
2. Adopting and Managing SBOMs
- Integrate SBOMs into SBOM Observer: Upload each version of the supplier components to SBOM Observer, either via the web interface or API.
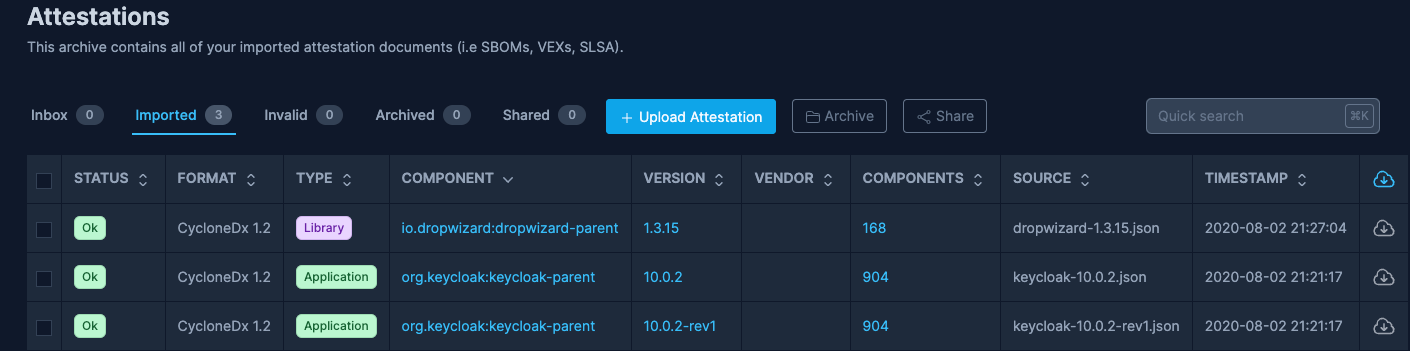
- Analyze SBOM Data: SBOM Observer automatically analyzes the uploaded SBOMs to identify vulnerabilities, licenses, and dependencies. Access an aggregated view of all vulnerabilities under Vulnerabilities in the main menu.
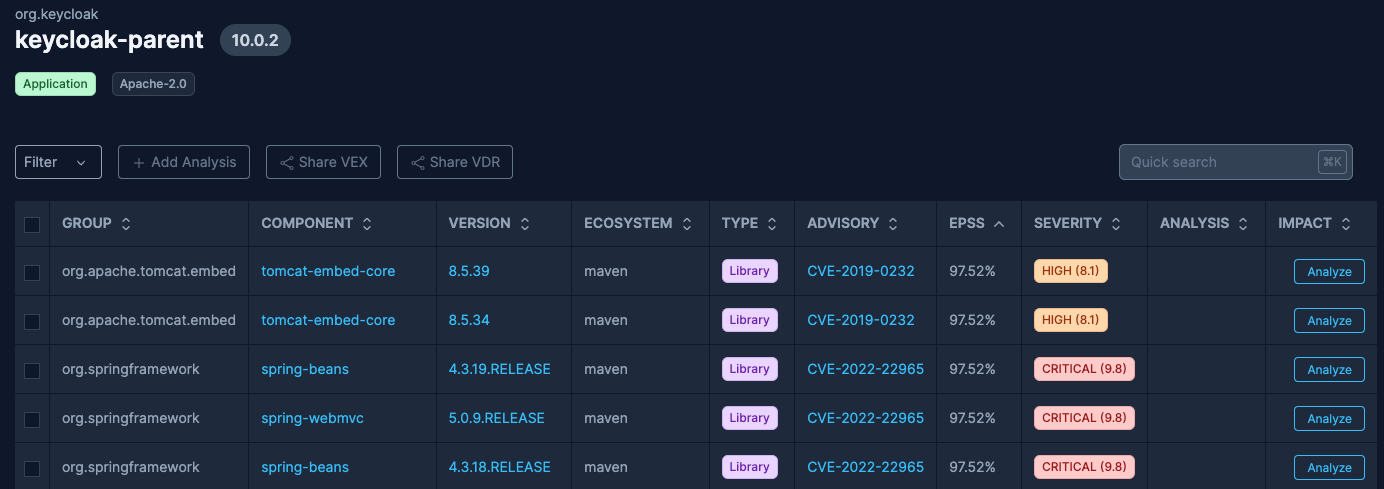
- Utilize Environments or Projects for specific scope analysis. Environments let you connect your software inventory to your operational model. Instantly see what vulnerabilities exist in your production environment, or what team is responsible for specific components.
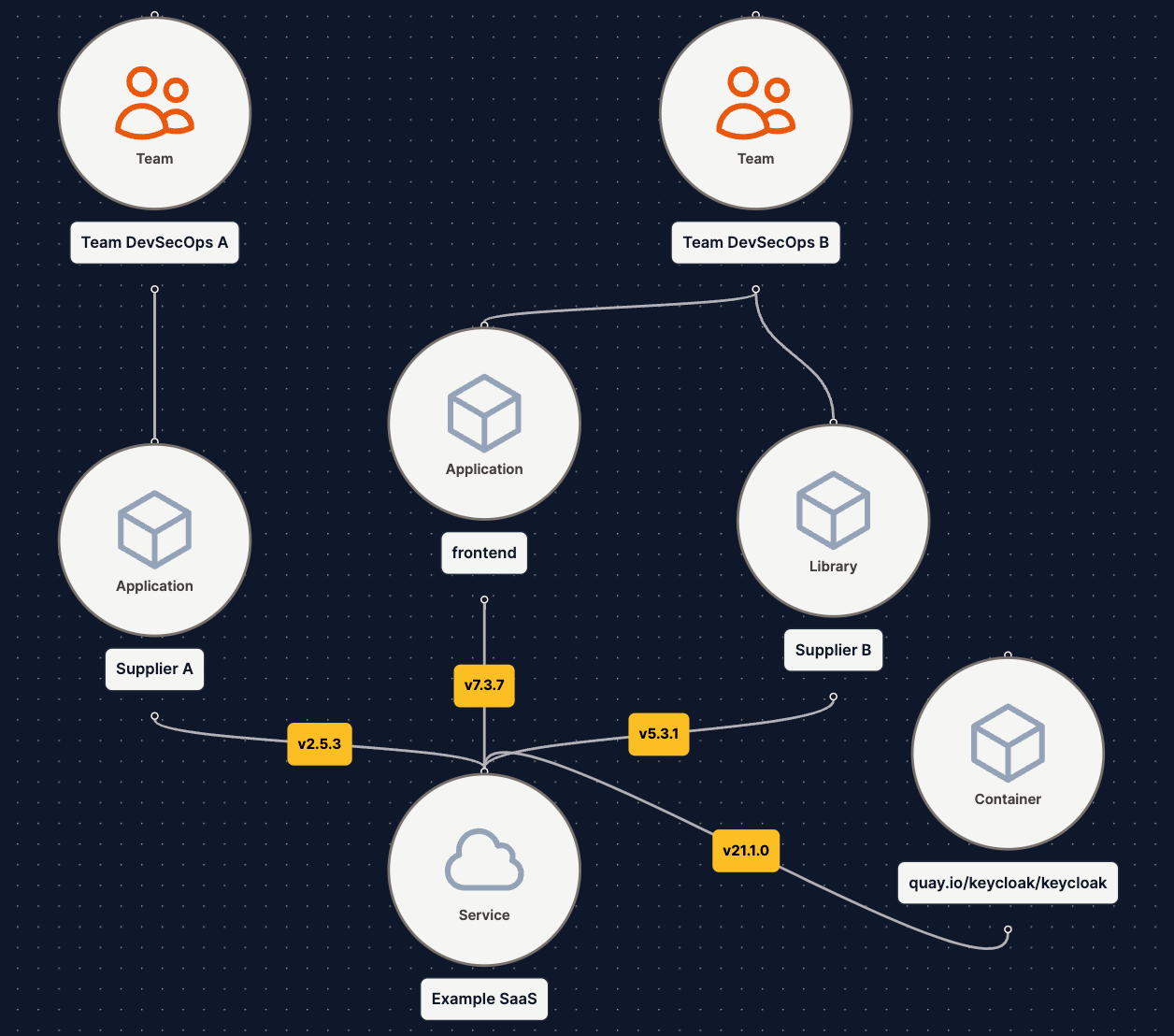 .
.
SBOM Archive: More Than Compliance
An SBOM Archive isn't just a compliance checkbox for regulations like DORA and Executive Order 14028; it's a strategic asset for your organization.
Whenever you add an SBOM all versions will be stored and you'll stay in control over time, streamlining risk management and enhancing security responsiveness.
3. Continuous Monitoring and Risk Assessment
- Continuous Monitoring: SBOMs in SBOM Observer are monitored continuously. With ecosystem coverage supporting over 25+ programming languages and operating systems, vulnerabilities in a vast array of tech stacks can be detected.
- Vulnerability Impact Analysis: Quickly answer questions like "Does this vulnerability impact our production environment?" or "Does this vulnerability affect our SLA customers?". Imported VEX data, along with manual analysis, is incorporated into visual representations for standardized impact assessments.
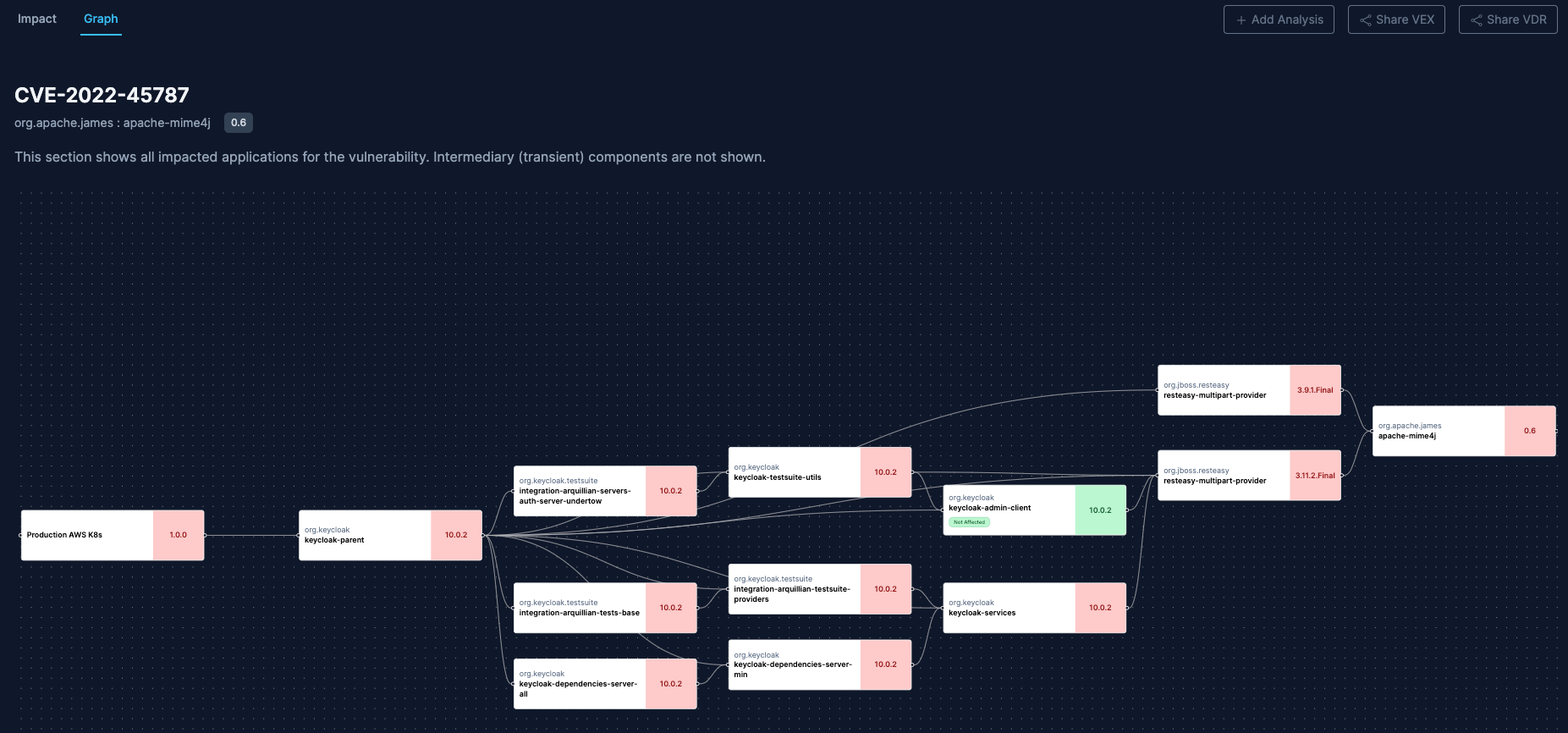
- Risk Assessments: Regularly assess risks associated with each supplier using SBOM Observer's Dashboard, which highlights recent security issues.
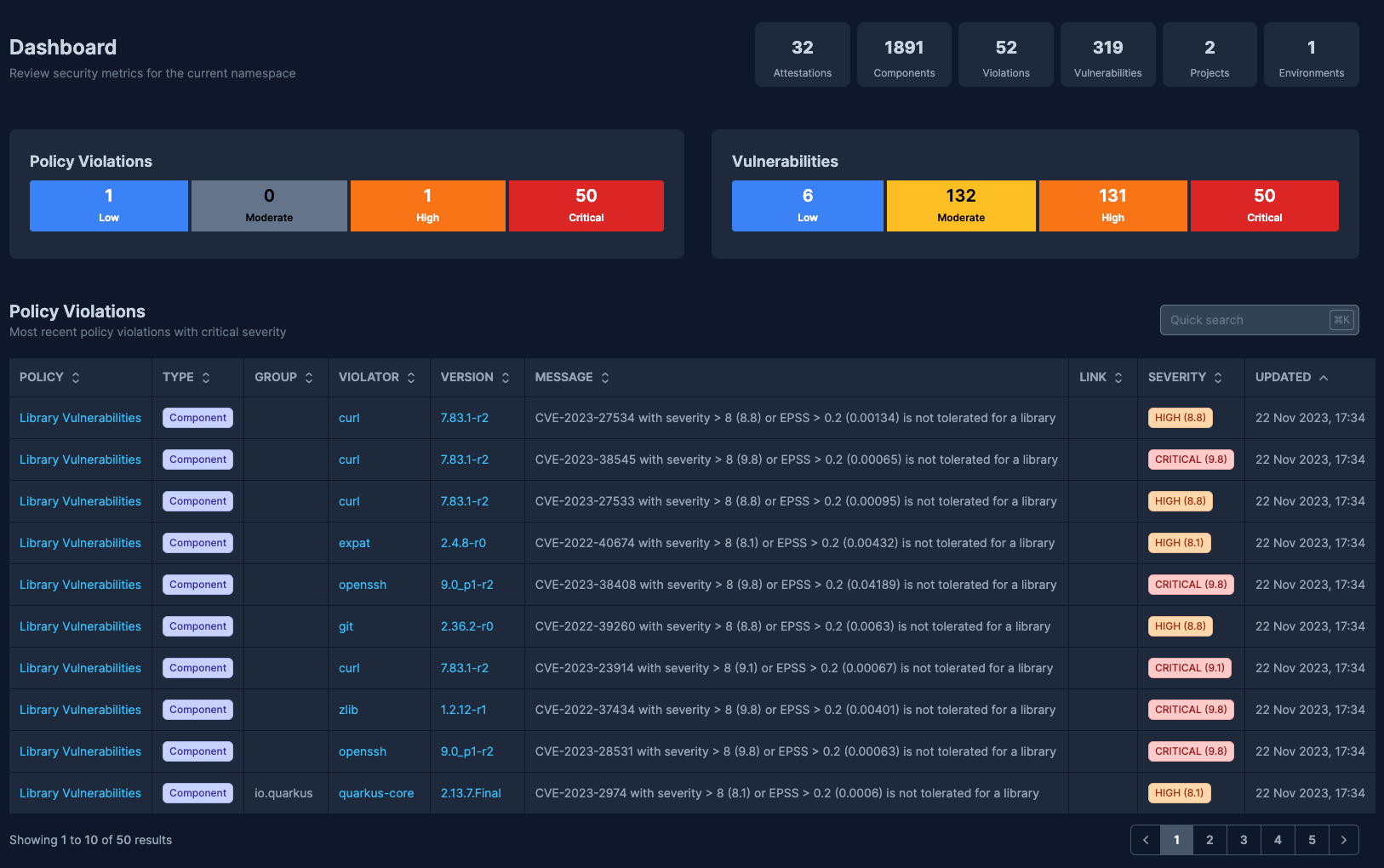
4. Managing Risk and Remediation (while saving time)
- Prioritize Critical Issues: Given the continuous influx of new vulnerabilities, focus on remediating the most critical ones first. Policies set at the component or attestation (SBOM) level can guide these priorities, ensuring compliance with both external regulations and internal policies.
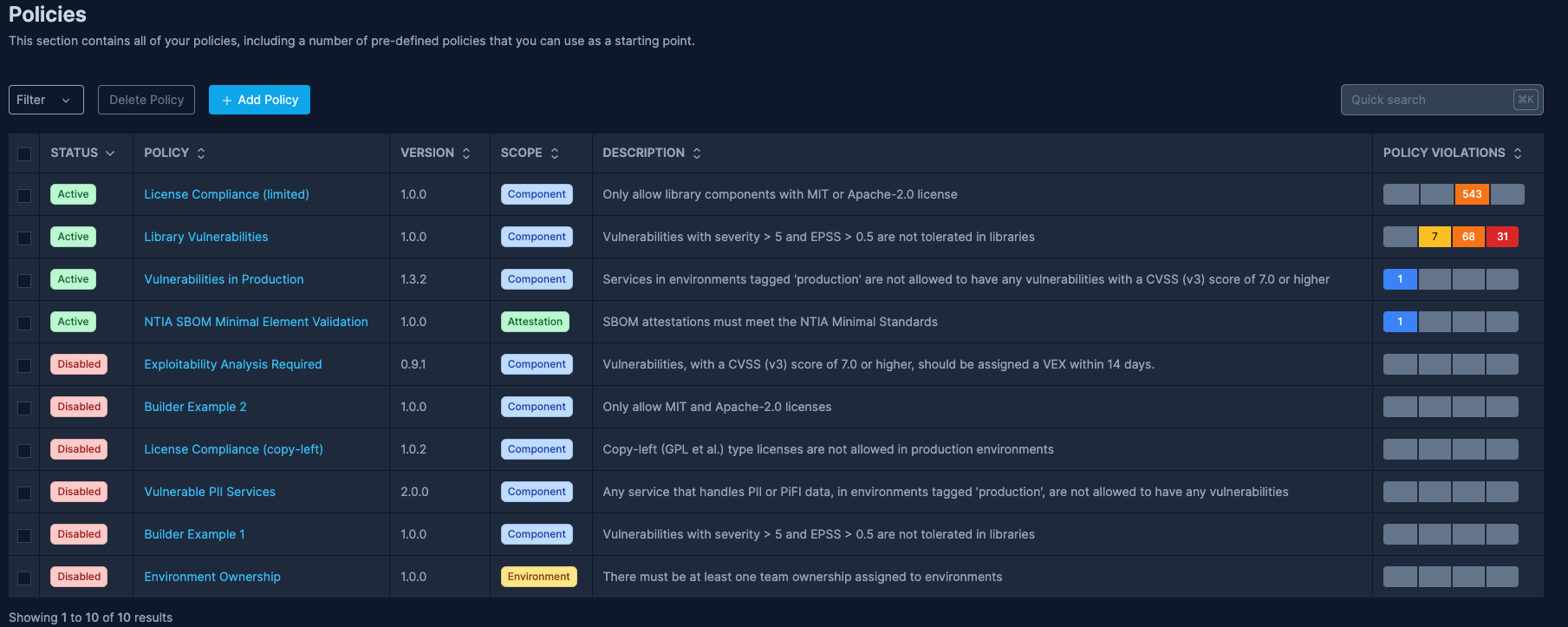
- Address Policy Violations: Manage policy violations to concentrate on critical issues, irrespective of their origin—be it vulnerabilities, license compliance, or impact on critical environments or customers. SBOM Observer's policy engine allows for policy definition as code and saves resources and time in addressing the sheer volume of new vulnerabilities.
