Step 4: Analyzing Findings and Vulnerabilities
With SBOMs in hand, you are well-positioned to dive into the critical process of vulnerability analysis. This step is vital for translating the transparency gained from SBOMs into actionable insights that will truly make a change.

Navigating Through Vulnerability Analysis
Understanding Vulnerability Analysis
Vulnerability analysis is the systematic examination of the components listed in your SBOMs (Software Bill of Materials) to identify known security weaknesses and potential risks. This process involves comparing the components against various vulnerability databases, such as the National Vulnerability Database (NVD) and more, to detect any matches with reported vulnerabilities.
Implementing Effective Analysis Practices
Automated Scanning: Leverage automated vulnerability scanning tools that can digest SBOM data and cross-reference it against vulnerability feeds that are continuously updated notifying you without delay when new vulnerabilities are discovered.
Prioritization: Not all vulnerabilities pose the same level of risk to your organization. Implement a prioritization mechanism based on factors such as the severity of the vulnerability (CVSS), the criticality of the affected asset (a crown-jewel?), and the context within which the asset operates (production or q/a?). Scoring models, such as EPSS, which indicate the likelihood of a vulnerability being exploited, can also be useful.
Continuous Integration: Utilize your existing CI/CD pipelines, so that updating an SBOM after you've fixed something doesn't become a chore. This way you will always have an up-to-date view of your current risk landscape and not be thinking along the lines: "did anyone close this vulnerability, or am I looking at outdated information?".
Cutting out the middleman: Make sure that once discovered, notifications of vulnerabilities are automatically sent to the team responsible for mitigation. Not doing so can create bottlenecks and prevent a timely response.
VEX - state of found vulnerabilities: Vulnerability Exploitability eXchange provides a standardized way to communicate detailed information about the exploitability of vulnerabilities. By integrating VEX into your vulnerability analysis process, you can communicate more informed decisions about remediation and mitigation. Read more about VEX here
Using SBOM Observer for efficient analysis
SBOM Observer significantly enhances the efficiency of analyzing findings and vulnerabilities within your software supply chain. By integrating SBOM Observer into your security strategy, you can streamline the vulnerability management process from detection to mitigation:
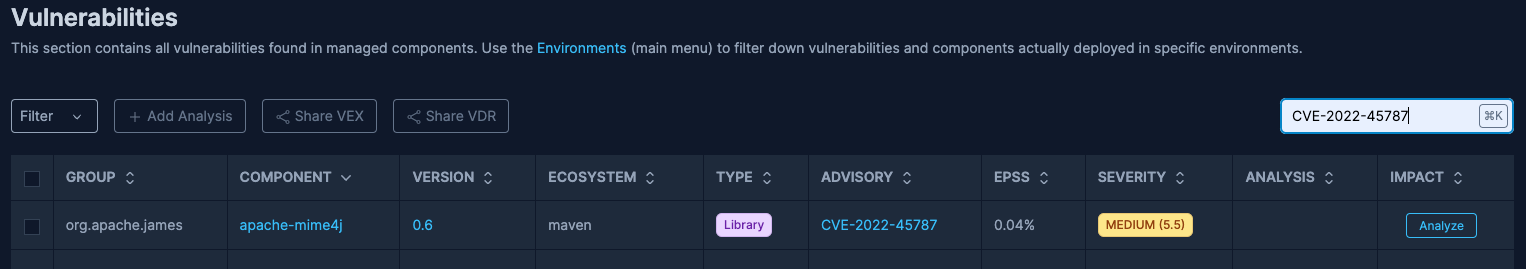
Automated Scanning: As a managed service, SBOM Observer processes your SBOM data and cross-references it against numerous continuously updated vulnerability feeds. This ensures you're notified without delay when new vulnerabilities are discovered, keeping your response time to a minimum.
Prioritization: SBOM Observer aids in implementing a robust prioritization by leveraging its policy-as-code features. Building on multiple measurements such as CVSS, EPSS and more offers a nuanced approach to prioritization.
Continuous Integration: SBOM Observer is designed to work seamlessly with your existing CI/CD pipelines, ensuring a continuously updated risk landscape view. Read more CI/CD pipeline integration using CLI, GitHub Actions or REST API here
"Cutting out the middleman": By defining what components belong to which team SBOM Observer ensures that the team, responsible for mitigation, receives relevant notifications. 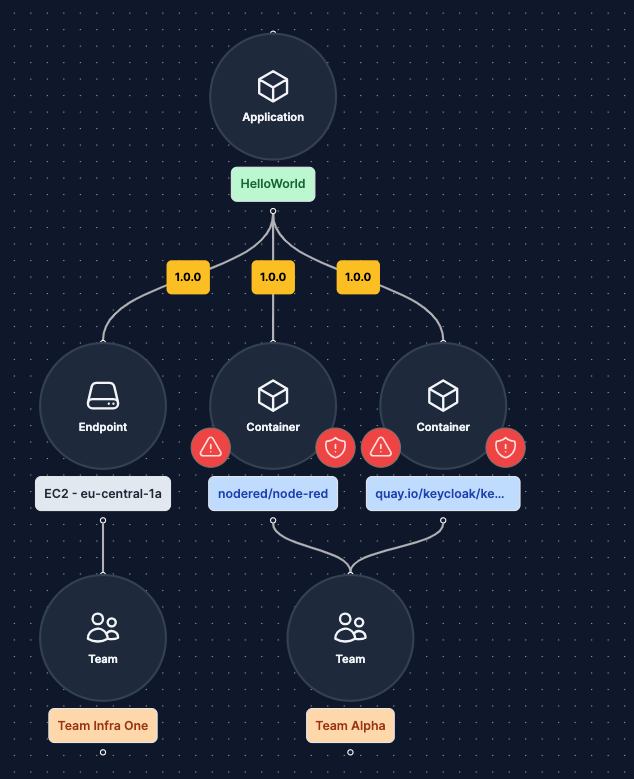
Leveraging Vulnerability Exploitability Exchange (VEX) to Streamline Vulnerability Management provides a standardized method to convey detailed exploitability information regarding vulnerabilities.

VEX provides a standardized way to communicate detailed information about the exploitability of vulnerabilities. By integrating VEX into your vulnerability analysis process, you can make more informed decisions about remediation and mitigation and if you are sharing your SBOMs to other parties. You can communicate the impact of found vulnerabilities to your stakeholder/customers using VEX. Learn more about VEX
Read more on SBOM Observer's Impact Analysis Feature
Next Step
In the next step, we explore how to manage risk early in the software development lifecycle (SDLC) - commonly referred to as "shifting left" effectively, using risk metrics.