Transform SBOMs into Enterprise-Wide Security & Compliance
Turn passive inventory into active control. With increased regulatory pressure across the software industry, automate compliance and prove security at scale.
Get a free IntroductionSBOM Management
Centralize SBOM operations across your software portfolio. Generate, ingest, and normalize SBOMs in SPDX or CycloneDX, and maintain a single source of truth for component inventory.
- Automated SBOM generation in CI/CD
- Generate SBOMs automatically for every build and release.
- Multi-format SBOM ingestion (SPDX & CycloneDX)
- Ingest and normalize SBOMs from vendors and internal teams.
- Vendor SBOM validation
- Validate SBOMs for completeness and quality.
- Component inventory dashboard
- Unified dashboard for all components and dependencies.
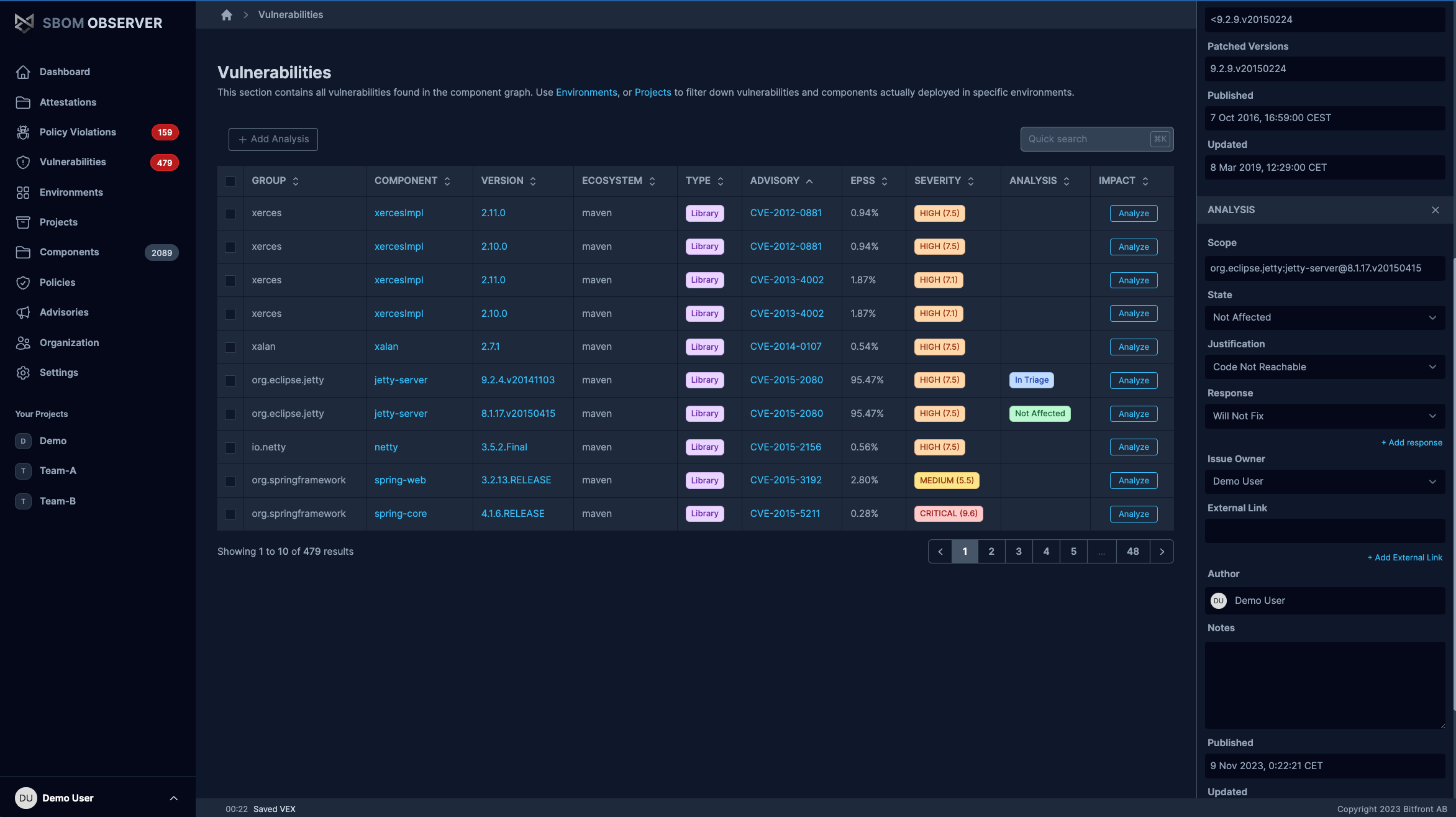
Vulnerability & Dependency Tracking
Move beyond raw CVE lists to understand real impact. Get actionable context with affected components and downstream impact analysis, and prioritize fixes based on business needs.
- Continuous vulnerability monitoring
- Monitor vulnerabilities across all tracked components.
- Exploit status & severity context
- Augment findings with context to focus work where it matters.
- Impact analysis with dependency graphs
- Visualize how vulnerabilities affect your software.
- Risk-based prioritization
- Prioritize fixes based on business and operational risk.
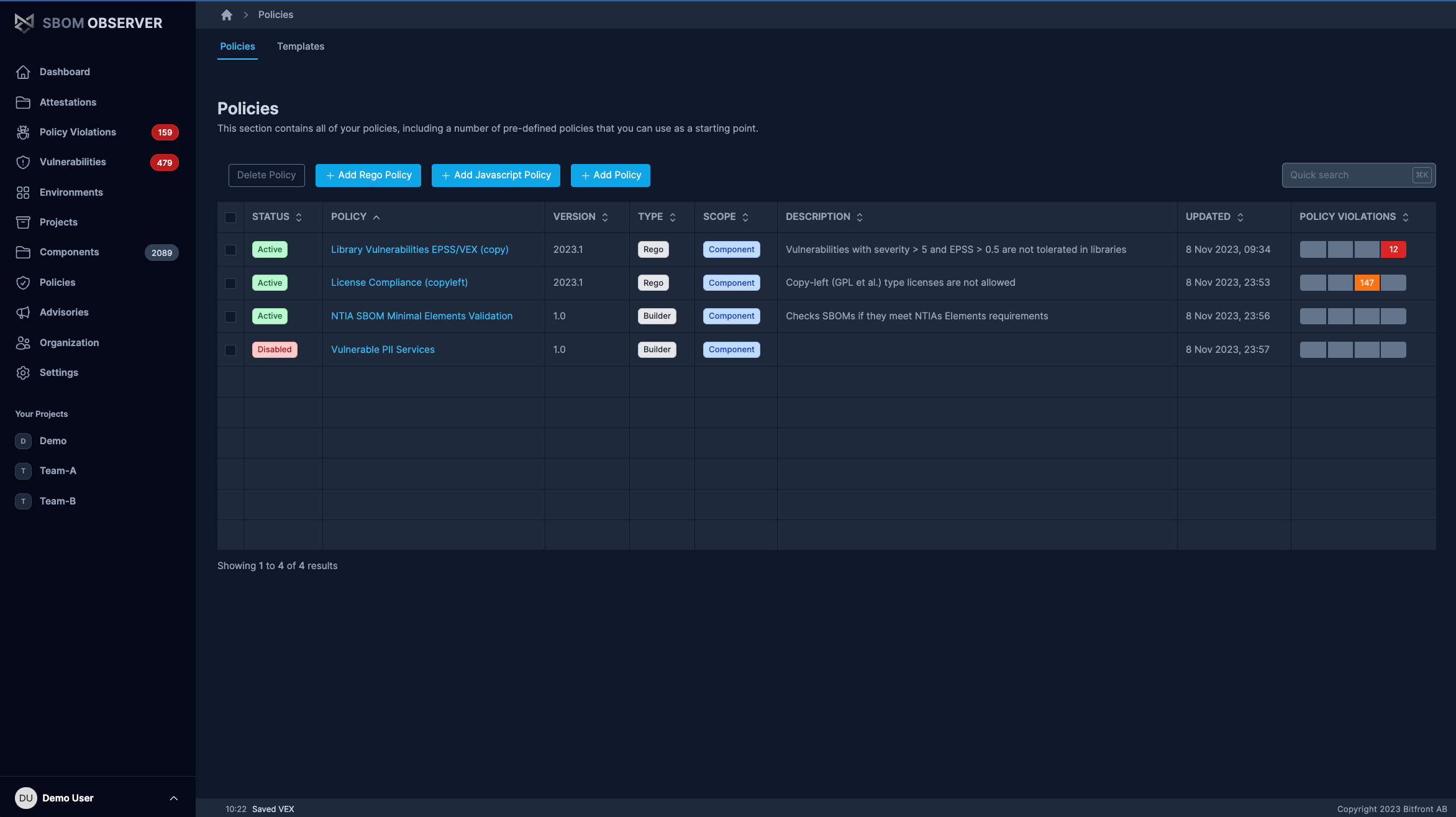
Policy Engine & Enforcement
Define policies and apply automated checks across your supply chain. Flag non-compliant components and surface violations early in development workflows.
- Flexible policies for regulations
- Align policies with DORA, CRA, NIS2, or customer requirements.
- Enforce policies in CI/CD
- Use the CLI to validate every release in your pipelines and fail builds automatically when violations are detected.
- Custom policy creation
- Create and manage security and compliance policies.
Compliance Alignment & Reporting
Support alignment with regulations such as DORA, CRA, and NIS2. Transform SBOM and vulnerability data into reports that help demonstrate compliance progress.
- Policy alignment support
- Use the policy engine to reflect regulatory and customer requirements.
- Evidence support
- Organize SBOMs, VEX, and VDR to support reviews and assessments.
- Release tracking over time
- Track each software release and its associated artifacts across versions.

Evidence & Artifacts
Generate and manage core supply chain artifacts including SBOMs, VEX, and Vulnerability Disclosure Reports (VDR). Maintain release-by-release visibility over what was shipped.
- VEX document generation
- Create VEX to communicate vulnerability impact and status.
- Vulnerability Disclosure Reports (VDR)
- Produce VDRs to share vulnerability handling details.
- Artifact lifecycle tracking
- Track artifacts across versions and releases.
- Internal sharing & review
- Enable teams to review artifacts alongside policy status.
DevSecOps Integrations
Integrate with your development workflows. Use the CLI in CI/CD to manage SBOMs and automate checks across popular platforms.
- CI/CD pipeline integration
- Integrate with major CI/CD platforms.
- Integrations via CLI
- Run Observer in GitHub, GitLab, Azure DevOps, and more using pipeline steps.
- CLI-based automation
- Automate Observer workflows via CLI in pipelines.
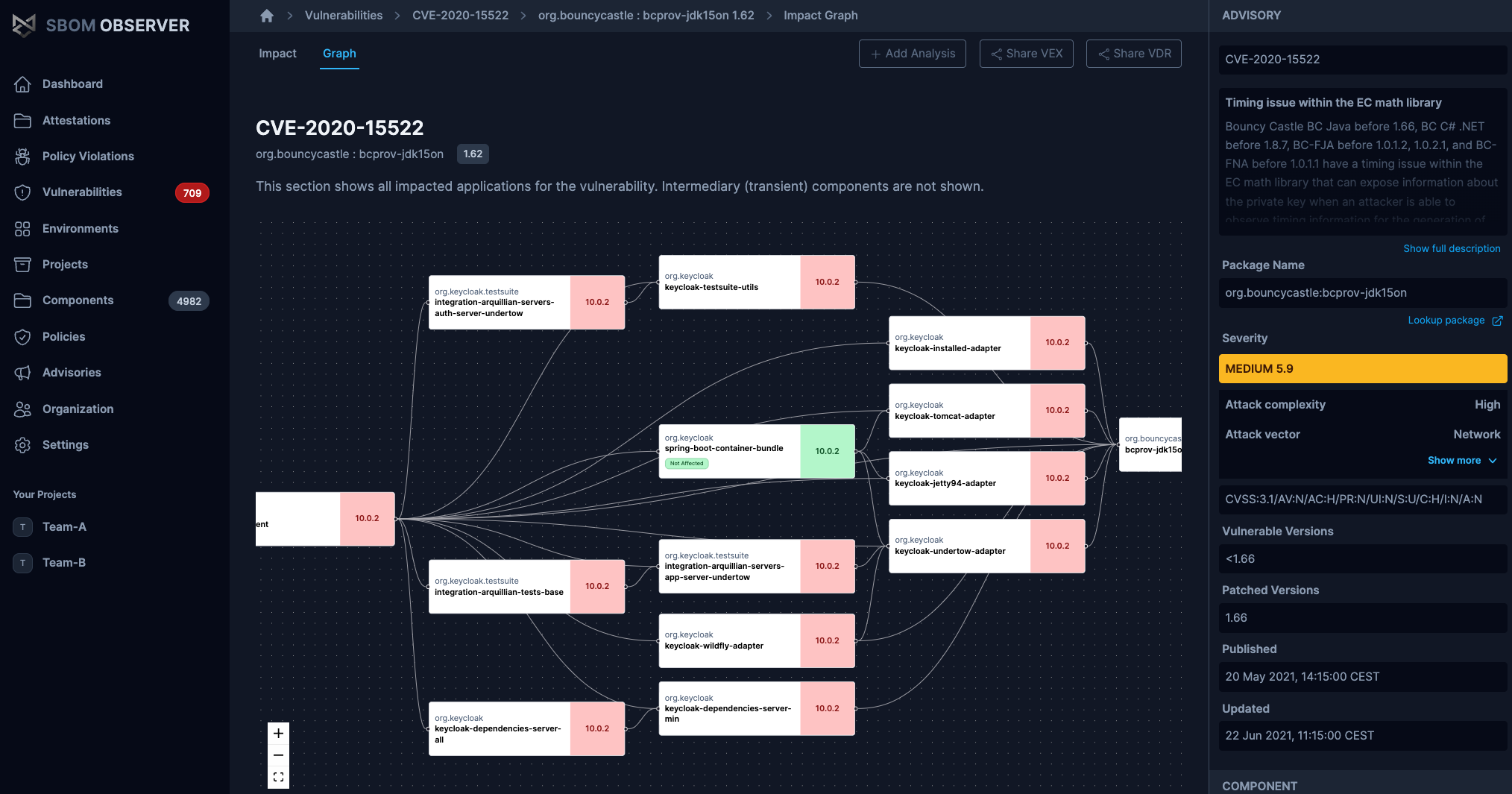
Risk & Impact Analysis
Visualize and quantify supply chain risk exposure. Explore dashboards that surface vulnerabilities and impacted components for specific applications and releases.
- Application vulnerability dashboards
- Dashboards that highlight vulnerabilities and affected components per application.
- Dependency impact analysis
- See how dependencies affect risk and compliance.
- Trend views over releases
- Understand how risk changes across versions and releases.
Ready to Take Control of Your Software Supply Chain?
Join security and compliance teams using SBOM Observer to transform software supply chain visibility and streamline regulatory alignment.
Platform Features
- SBOM Management
- Create, Import, Share and Manage SBOMs throughout the software development lifecycle. Full support for standards such as CycloneDX, SPDX, VEX.
- SLSA Support
- While SBOMs provide you with an inventory, SLSA (Supply-chain Levels for Software Artifacts) enables you to track artifact integrity, that the source code you’re relying on is the code you’re actually using, across your software supply chain.
- Vulnerability Detection
- Detect known vulnerabilities in your inventory of applications, components and containers across wide selection of ecosystems. We integrate many of the standard advisory sources, including GitHub, OSV and NVD.
- Exploitability Analysis (VEX)
- Triage and add vulnerability explotability analysis ('Is this exploitable in this particular application?') to detected vulnerabilities, and share findings with your customers.
- Policy-driven Compliance
- Codify your security and quality policies and enforce them across your entire SDLC with a powerful Policy Engine based on Open Policy Engine (OPA).
- Policy as Code
- In addition to our visual policy builder, DevSecOps professionals can leverage their existing skill set and drop down to Rego or JavaScript when implementing policies.
- Operational Model
- Connect your organizations internal view of teams, services, applications, containers and deployments with the inventory provided by SBOMs and other tools.
- Track Releases
- Track deployments of releases to production environments in the operational model and leverage that information in policies - reducing the noise and helping prioritization of vulnerabilities and violations.
- CI/CD
- Easily integrate your CI/CD pipeline using popular tools and our broad support for SBOM standards and ready made solutions (Observer CLI).
- Automatic Discovery of Applications
- Automatically synchronize your operational model integrations for Kubernetes and AWS ECS, making sure you have an up to date picture of what is running in production. (On the roadmap)
- Exploit Prediction Scoring
- Use the Exploit Prediction Scoring System (EPSS) in combination with the Operational Model and other threat signals to prioritize remediation of detected vulnerabilities.
- CISA VEX
- Create and share CISA compliant Vulnerability Exploitability eXchange (VEX) data to communicate the exploitability of vulnerable components in the context of the product customers or partners are using.
Talk to our team about your SBOM needs
Tell us about your challenges — we'll show how SBOM Observer fits your workflow.