Automate compliance and security
Track risk. Enforce policy. Prove compliance.
Go beyond SBOM generation. SBOM Observer helps you enforce policies, track vulnerabilities, and deliver evidence accepted by regulators, customers, and your team.
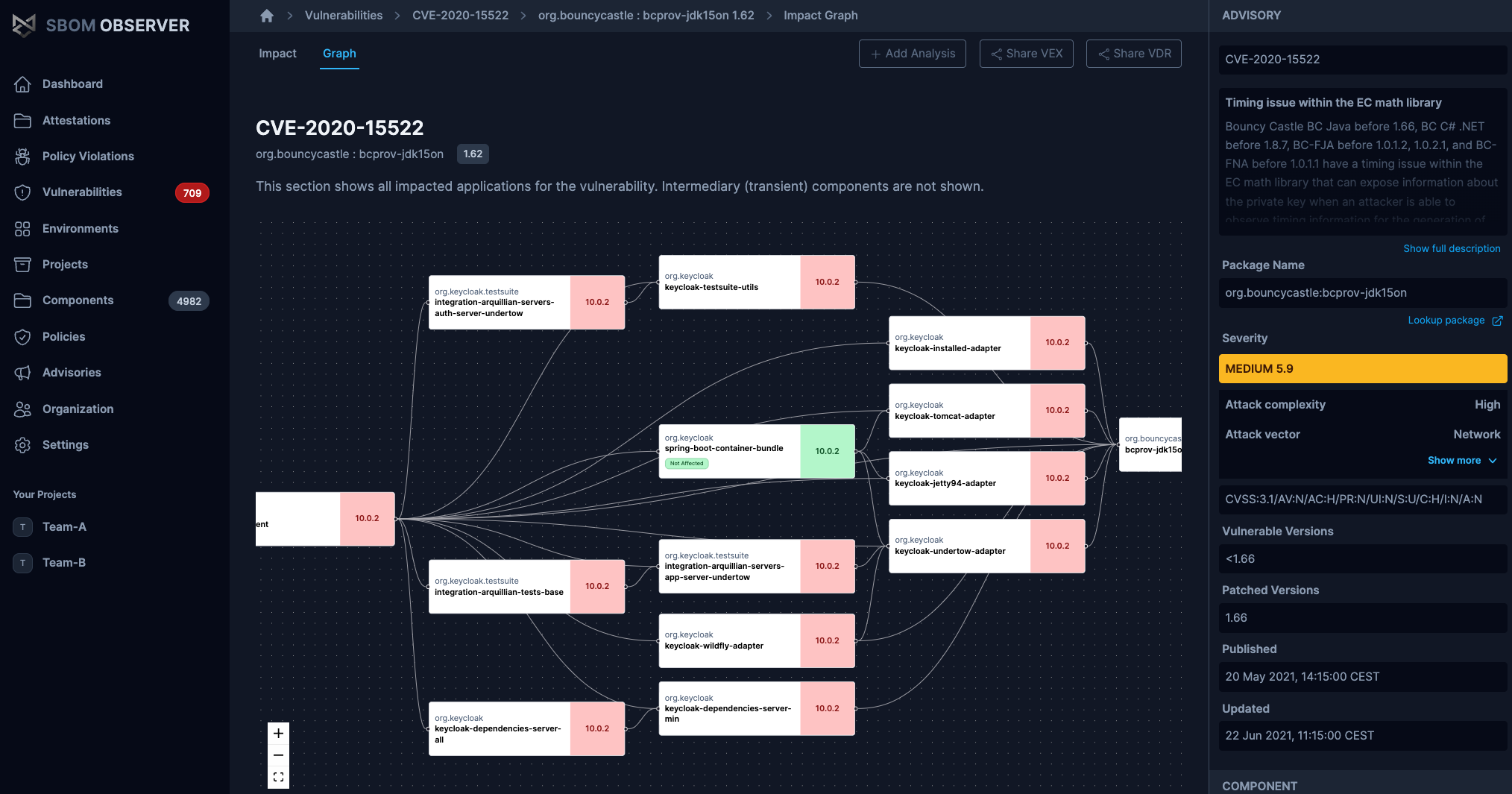

Software Supply Chains Demand Proof
Proof is not optional
Third-Party Risk Is on the Radar
Procurement and security teams now expect vendor SBOMs, vulnerability posture, and license obligations. Unify vendor SBOMs and controls to show what's compliant and what needs action.
Customers Demand Answers
Security reviews go deeper. Buyers expect SBOMs, clear policies, and proof your software meets their risk requirements. Automate policy validation and provide SBOMs and compliance status on request.
Regulators Are Raising the Bar
DORA, NIS2, CRA, and EO 14028 require supply chain transparency and secure development. Map your controls to these rules, enforce them in CI/CD, and generate audit-ready evidence.
Manual Work Can't Keep Up
With thousands of new vulnerabilities each month and fragmented tools, teams struggle to prioritize real risks. Normalize SBOMs and focus on what is actually affected.
Go Beyond the SBOMs. Operationalize Compliance.
SBOM Observer provides a complete platform for managing software supply chain risk and compliance
Complete Visibility
See every component across your software portfolio in one place. Unify internal and vendor SBOMs for a complete view of supply chain risk.
Automated Compliance
Map policies to frameworks like DORA, CRA, and NIS2. Enforce compliance directly in your CI/CD workflows.
Continuous Monitoring
Detect vulnerabilities early and reduce risk with automated checks and continuous monitoring.
Streamlined Operations
Eliminate spreadsheets and fragmented tools. Run compliance, monitoring, and reporting from one automated platform.
Trusted by Modern Software Teams
Why Choose SBOM Observer?
Built to make software supply chains transparent and compliant
Built for SBOM-Centric Workflows
Purpose-built for SBOM analysis and compliance — covering the full lifecycle from ingestion to reporting.
Proof Engine
Keep track of all your SBOMs at scale — every version, across all releases, for both internal components and vendor software.
Unified View
Bring internal and vendor SBOMs together in a single dashboard. No more silos or scattered spreadsheets.
Framework Aligned
Focused on helping customers align policies with evolving regulations and stakeholder demands.
Developer Friendly
Work the way you prefer — through CLI or UI — with seamless integration into your CI/CD pipelines.
Open Standards
Manage your SBOMs with open standards at the core — SPDX, CycloneDX, and VEX for portability and compliance.
Frequently Asked Questions
Can’t find the answer you’re looking for? Reach out to our team.
- Can SBOM Observer help us comply with DORA, NIS2, or EO14028?
- Absolutely. Our platform aligns directly with regulatory frameworks like DORA, NIS2, CRA, and EO14028. You can start from policy templates, enforce them in your workflows, and generate audit-ready evidence — all in one place.
- Can I integrate my current SCA tool with SBOM Observer?
- Yes. SBOM Observer is compatible with most SCA tools and supports SBOMs in CycloneDX and SPDX formats. We ingest their output into our policy and compliance workflows.
- Is SBOM Observer a scanner or a platform?
- It's a platform. While we provide an open-source tool for SCA, our core value is in automating policy enforcement and proving compliance through SBOM-centric workflows.
- Do you support vendor-provided SBOMs?
- Yes. You can ingest SBOMs from third-party vendors, validate them against a policy, and include them in your unified compliance view — alongside your own software artifacts.
- Is on-premise deployment available for SBOM Observer?
- Yes. SBOM Observer supports secure on-premise installations, optionally air-gapped, for organizations with privacy, compliance, or connectivity requirements. Reach out to our to learn more.
Ready to transform your software supply chain?
Book a demo to see how we can help you achieve your goals.